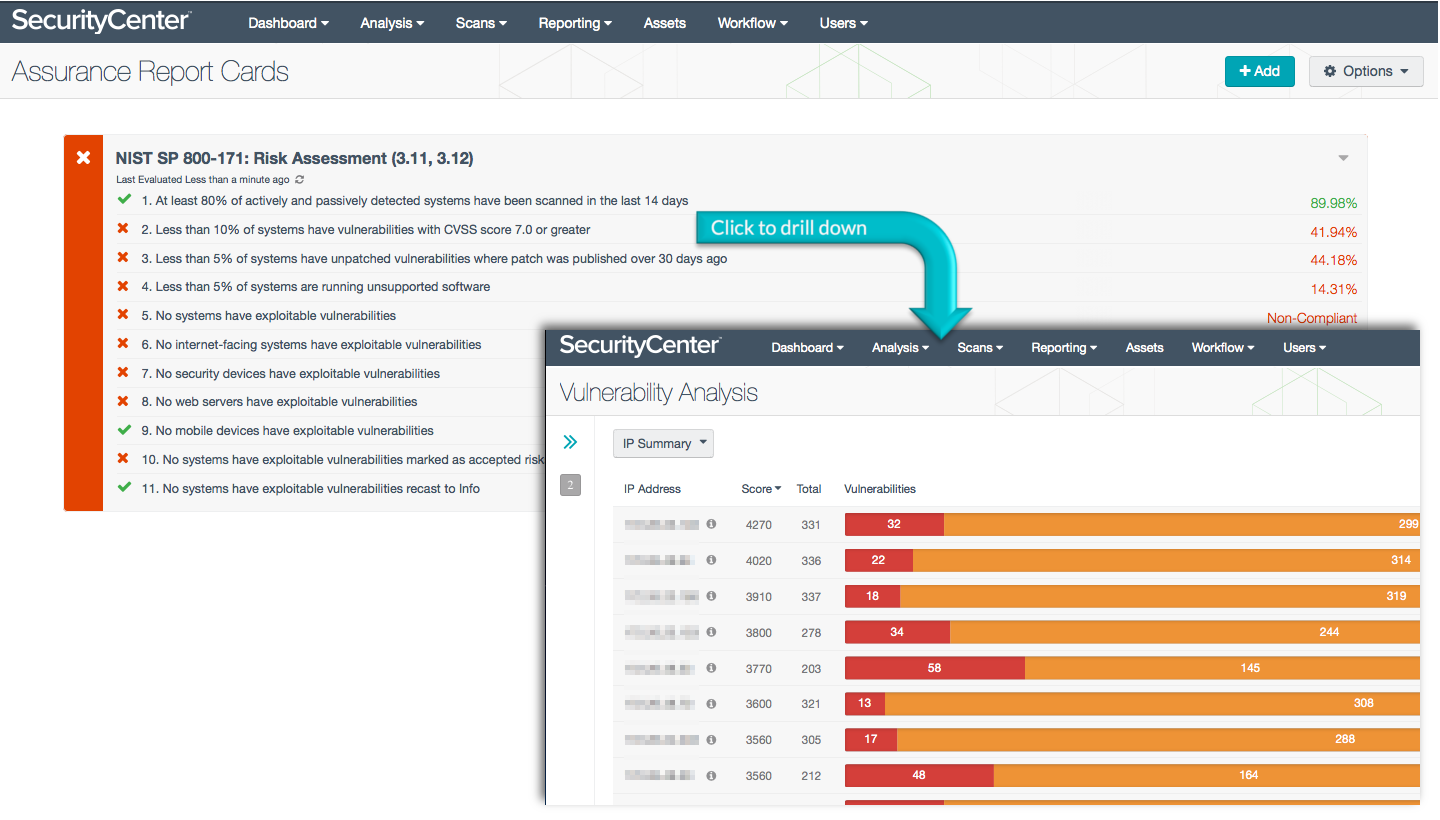
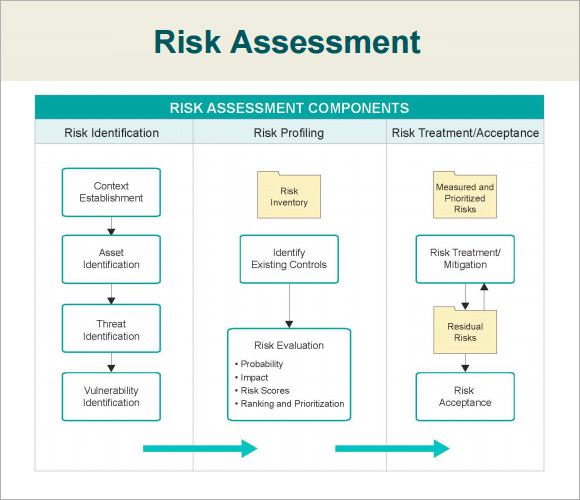
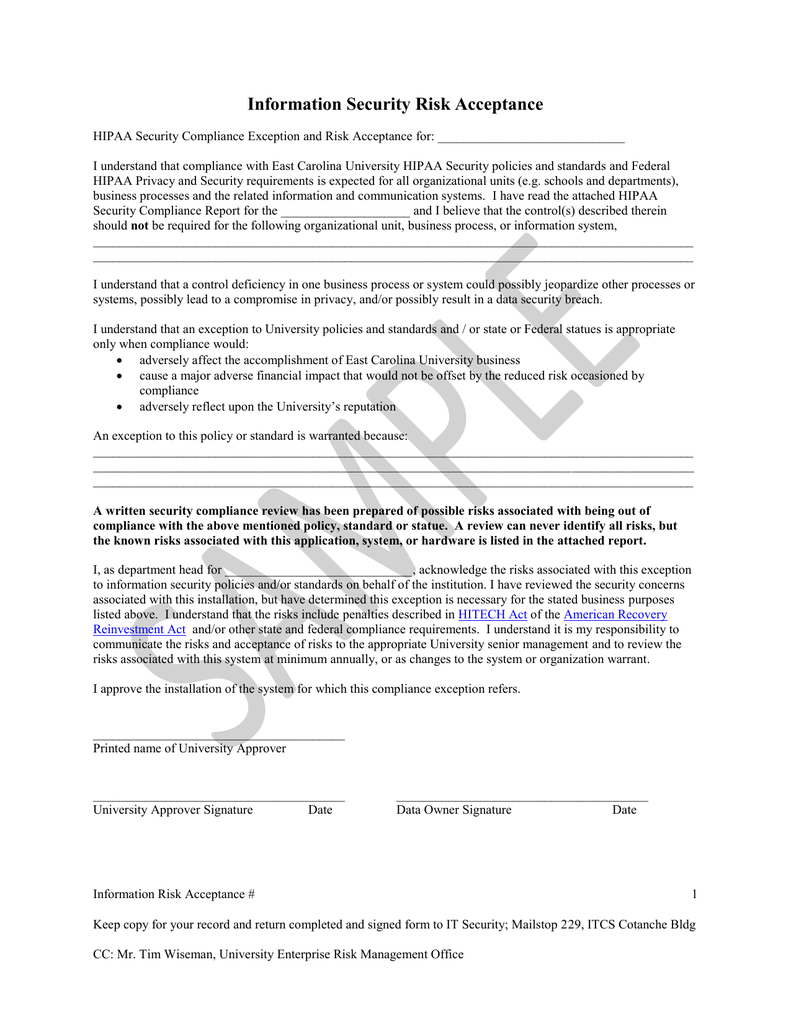
Risk Acceptance Form Nist
Risk Acceptance Form Nist - Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. The system/project manager is responsible for writing the justification and the. 1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. This form is used to justify a risk acceptance of a known deficiency. Next, provide a detailed justification.
1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. The system/project manager is responsible for writing the justification and the. This form is used to justify a risk acceptance of a known deficiency. Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. Next, provide a detailed justification.
Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. This form is used to justify a risk acceptance of a known deficiency. Next, provide a detailed justification. The system/project manager is responsible for writing the justification and the. 1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp.
Risk Acceptance Template Automate it airSlate
Next, provide a detailed justification. This form is used to justify a risk acceptance of a known deficiency. 1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. The system/project manager is responsible for.
Nist 800 Risk Assessment Template Nist Policy Templates
Next, provide a detailed justification. Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. 1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. This form is used to justify a risk acceptance of a known deficiency. The system/project manager is responsible for.
Risk Acceptance Form — RCFL
Next, provide a detailed justification. Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. 1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. This form is used to justify a risk acceptance of a known deficiency. The system/project manager is responsible for.
NIST Risk Management Framework Aligns Privacy, Risk and Security
Next, provide a detailed justification. This form is used to justify a risk acceptance of a known deficiency. The system/project manager is responsible for writing the justification and the. 1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. Form shall be used when requesting a waiver or risk acceptance for an.
Fillable Online Risk Acceptance Form Example Fill Online, Printable
1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. Next, provide a detailed justification. The system/project manager is responsible for writing the justification and the. This form is used to justify a risk acceptance of a known deficiency. Form shall be used when requesting a waiver or risk acceptance for an.
Nist 800 30 Template
1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. The system/project manager is responsible for writing the justification and the. This form is used to justify a risk acceptance of a known deficiency. Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness..
Nist 800 Risk Assessment Template / Information Security Risk
The system/project manager is responsible for writing the justification and the. Next, provide a detailed justification. Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. This form is used to justify a risk acceptance of a known deficiency. 1) describe the compensating controls that will be implemented and, if applicable, the.
Risk Acceptance Form Template DocTemplates
Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. The system/project manager is responsible for writing the justification and the. Next, provide a detailed justification. 1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. This form is used to justify a risk.
Risk Acceptance Powerpoint Ppt Template Bundles PPT Slide
This form is used to justify a risk acceptance of a known deficiency. Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. Next, provide a detailed justification. 1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. The system/project manager is responsible for.
Information Security Risk Acceptance Document
1) describe the compensating controls that will be implemented and, if applicable, the control number from nist sp. This form is used to justify a risk acceptance of a known deficiency. The system/project manager is responsible for writing the justification and the. Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness..
1) Describe The Compensating Controls That Will Be Implemented And, If Applicable, The Control Number From Nist Sp.
Next, provide a detailed justification. This form is used to justify a risk acceptance of a known deficiency. Form shall be used when requesting a waiver or risk acceptance for an information system (is) security weakness. The system/project manager is responsible for writing the justification and the.